Before we begin, remember that this tutorial us only for educational purposes only, so you can learn how can hackers hack your instagram account, and how to prevent it.

Instagram has been a target of a lot of hackers lately. Millions of people’s accounts has been on Instagram (I’ll admit, I hacked a few myself, sorry guys, but curiosity. Plus I gave the owners access back.). A lot of people use Instagram, most of them teenagers who have no knowledge of the hacking world, which makes the platform attract a lot of hackers. Plus Instagram doesn’t really have very good security, especially when it comes to bruteforce.
So it’s been quite easy to hack Instagram. Even for script kiddies, with no knowledge of hacking or programming, who download bruteforce or phishing scripts from github. Not only that, but even normal people with no knowledge of hacking whatsoever can get started with it, thanks to the free scripts on github and termux which makes it easy to get started with Linux.
Today, I will share two popular methods which people and hackers use to hack instagram accounts. It’s not a 100 percent guaranteed way, it never is in hacking world, but if you have the skills and some social engineering knowledge, it’ll increase the odds of a successful attack. So let’s get started
Method 1: Bruteforce
The most famous method of hacking social media accounts. Bruteforce is when a hacker uses a script that automates the login process, but in this case, the script uses a wordlist of passwords and keeps trying to login, hoping one of the combination of passwords is the correct one. You might be asking, what the hell is a wordlist? Well, a wordlist is a text file containing a number of passwords (can be 100 or a million) that the hacker generates based of off the info they collected from you.
For example, they take your pet name, birth date, name and etcetera, and they mix it up (like hayley2010) to generate possible password combinations. Most of the time, a hacker does this using a wordlist generator script (cupp), which generates millions of possible password combinations in seconds. So once the wordlist is generated, the script tries to log in with each password.
Here are the steps you need to take to do a brueforce attack (you can skip steps 1 to 4 if you have already configured termux):
Step 1: install Termux on your phone. (Click here to download)
Step 2: update the environment by typing: “pkg update && pkg upgrade” without the quotes.
Step 3: install git by typing: “pkg install git”
Step 4: install python by typing: “pkg install python3” or “pkg install python”
Step 5: install the bruteforce tool by typing “git clone https://github.com/Bitwise-01/Instagram-” note that you can use any other bruteforce tool, I’m using this because it works, and is easy to use.
Once the script is installed, navigate to it’s folder by typing “cd Instagram-“. You must enter it exactly like that. Once inside the folder, type “ls” to see the contents. Now we need to install the required files for the script to function properly. We can do this by typing “pip3 install -r requirements.txt”. Wait for it to finish.
Step 6: create a wordlist file. As I mentioned before, a wordlist is just a text file with a bunch of passwords to try. to create a wordlist, we need a command line text editor. Type “pkg install nano” to install nano text editor. Once it’s done, type “nano wordlist.txt” this will create a text file called wordlist.txt and open it. Now type the passwords you want the script to try. Each password needs to be in a new line, like this:

Once you’re done writing the passwords, click on CTRL button and x on the keyboard. It’ll ask if you wanna save it. Type y and press enter
Note that you can also install cupp to automatically generate a wordlist. Just type “git clone https://github.com/Mebus/cupp” to install and cd into the folder and run cupp.py
Step 7: now that the wordlist file is created, it’s time to perform the attack
Type “python3 instagram.py username wordlist.txt” remember to replace the “username” with the username of the person you wanna hack.
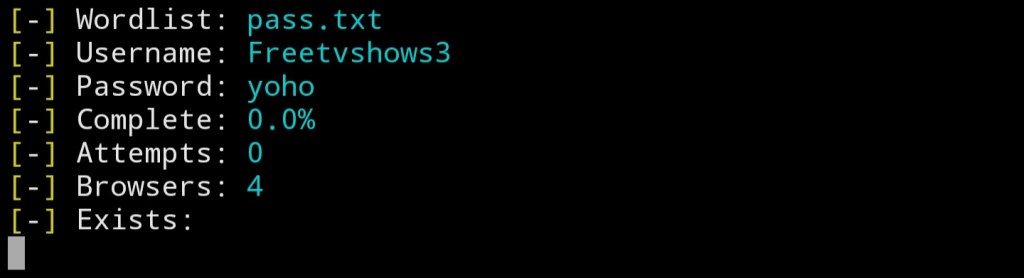
Now the script has started working, it’ll try to login with each password until it finds the right one.
Once it does, it’ll let you know.
And that’s how you perform a bruteforce attack.
Method 2: Phishing Attack

There are different ways to do a Phishing Attack. You can send a fake email message to your target, saying they’re instagram has been hacked and they need to login to reset the password and take back control, which will lead to target enter his/her password in the fake login page. Or you can try chatting them and coming up with a social engineering trick to make them log in to a fake Instagram login page.
The one universal thing for phishing is the fake login page, which saves the entered credentials and redirects them to a real login page.
The easier method is to chat them up on insta and make them login.
You only need two things to do a phishing attack. Some social engineering skills and a fake login page.
Note: once you do get the targets credentials, try to use a VPN to connect to wherever they are (for example, if they are from New York, connect to a New York VPN) while logging in, to prevent Suspecious login page.
You can go to this article to read more about how to create a fake login page for instagram and do a phishing attack. Or you can install shellphish and do it yourself, it’s fairly similar to a bruteforce attack, you run a script on termux, it gives a link, you send the link to target and they login, you get the credentials.
There are other ways to hack an insta account, such as install a Remote Administration Tool (or RAT) to take control of the targets phone, which then allows you to see instagram messages or by installing a Keylogging software, which saves everything the target types, and sends it to you.
Read this article to learn more about RATs and this article to learn about Keylogging and good luck.
If you got any question, or ran into any problems, do let me know and I’ll try to help.

One reply on “How To Hack Instagram Using Termux (Working 2021)”
instagaram
LikeLike