
In the field of Cybersecurity, you have to make use of tools to do your job. there are a lot of different programs and software’s, both open source and closed, that a hacker can use to do different tasks, such as enumeration, reconnaissance, post exploitation and more.
while there are plenty of software’s, made by programmers and hackers, hosted on github.com to do a specific task, most of them tend to not be as efficient or powerful as the ones commonly used. in this articles, i will list top 10 most popular and essential tools you will need to use to be a professional hackers. note that these tools are also used by almost every professional hacker.
- Metasploit
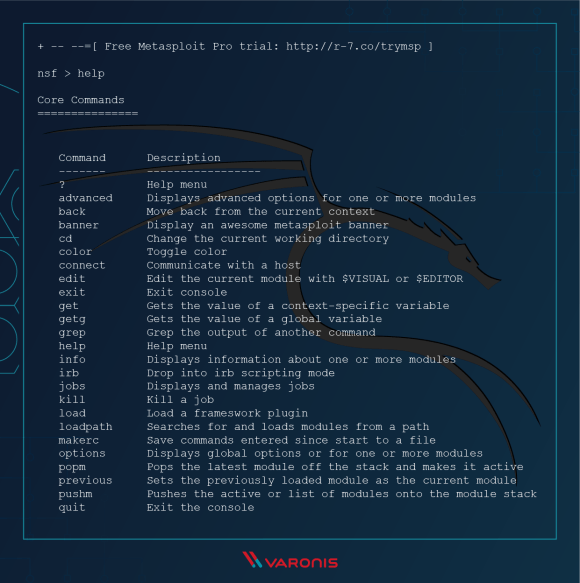
Platforms: Windows, Linux, Mac OS
Price: Metasploit Framework is free, Metasploit Pro is paid
Type: Security
Link: Link
Best For: Building anti-forensic and evasion tools.
Description: Metasploit Framework is a powerful tool that can be used by black hats and ethical hackers. because it’s open source, it can easily run on any operating system. metasploit contains different modules such as:
- Exploit (tool used to take advantage of a system weakness)
- Payloads (sets of malicious code)
- Auxiliary Functions (supplementary tools and commands)
- Encoders (used to convert code and information)
- Listeners (malicious code that hides in order to get access)
- Shell code (code that is programmed to activate when inside the target)
- post-exploitation code (code that is used to test deeper penetration once inside)
- Nops (an instruction to keep the payload from crashing)
2. Nmap
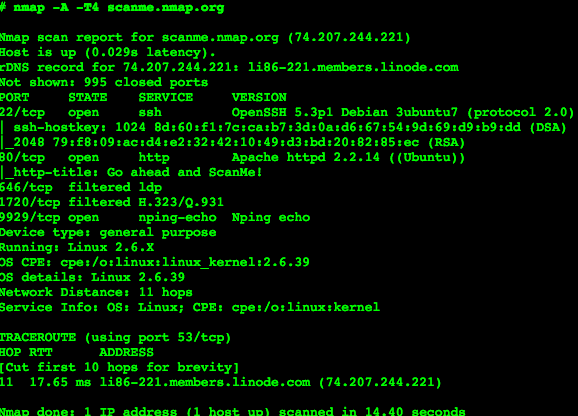
Type: Computer Security and Network Management
Platform: Windows, Linux, Mac OS, Solaris and OpenBSD
Price: Free
Link: Link
Best for: Scanning networks for weaknesses
Description: Nmap is a free and popular tool that is often used to scan networks and search for open ports. it’s an open-source software that was created by Gordon Lyon. Nmap can also be used to detect Operating System of a target device as well as Host Discovery.
3. Wireshark
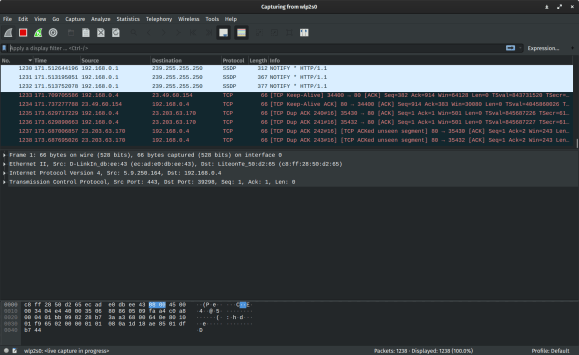
Type: Packet analyzer
Platform: Linux, Windows, Mac OS, FreeBSD, NetBSD, OpenBSD
Price: Free
Link: Link
Best For: Analyzing and capturing data packets
Description: Wireshark is also a popular hacking tool best used to capture and analyze packets. you can use wireshark to capture any incoming or outgoing packet and then analyze to see what data the packets contain. black hat hackers usually use wireshark to analyze the packets of a public wifi to capture people private data, like social media info and more.
Also Read: How To Install Kali NetHunter on any Android Phone
4. Aircrack-Ng
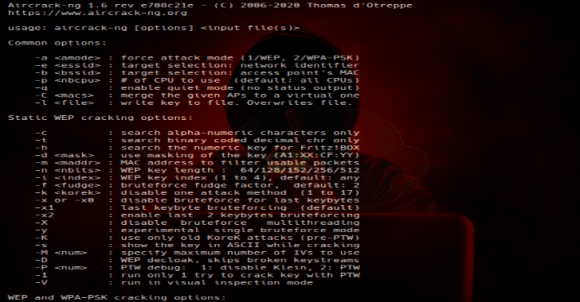
Type: Packet Sniffer and Injector
Price: Free
Platform: Cross Platform
Link: Link
Best For: Building anti-forensic and evasion tools.
Description: it’s a network software suite consisting of WEP, WPA,WPA2 cracker, detector, packet sniffer and analyzer. it’s free, open source and cross platform. often used to inject packets and crack vulnerable WEP systems and brute-force WPA and WPA2 wifis. it comes pre build with some linux OS’s such as Kali Linux and Parrot Security OS.
5. BurpSuite

Type: Application Security Testing Software
Platform: Mac OS, Linux, Windows and .JAR Versions
Price: Free and Paid versions available
Best For: Testing Application Security
Link: Link
Description: BurpSuite is a leading range of cybersecurity tools and software’s made by PortSwigger. BurpSuite comes with tools such as:
- Automated web security scan
- editing and repeating requests
- decoding data and much more
6. Netsparker

Type: Web Application Security Scanner
Platform: Cross Platform
Price: Free and Paid Versions available
Best For: Scanning for vulnerabilities of a web application
Link: Link
Description: Netsparker is an automated but fully configurable web application security scanner. it is used to automatically scan for a web application or website to see if it’s secure or not. but it is often used by black hat hackers to check for websites weaknesses or vulnerabilities. it is also the only network security scanner that automatically exploits any vulnerabilities found.
7. Ettercap

Type: Computer Security
Platform: Cross Platform
Price: Free
Best For: Creating custom plugins
Link: Link
Description: etterccap, which supports cross platform, is used to create custom plugins. it can also do sniffing of https SSL, even with proxy connection. some of it’s features include:
- Sniffing of live connections
- Content filtering
- Active and passive dissection of many protocols
- Network and host analysis
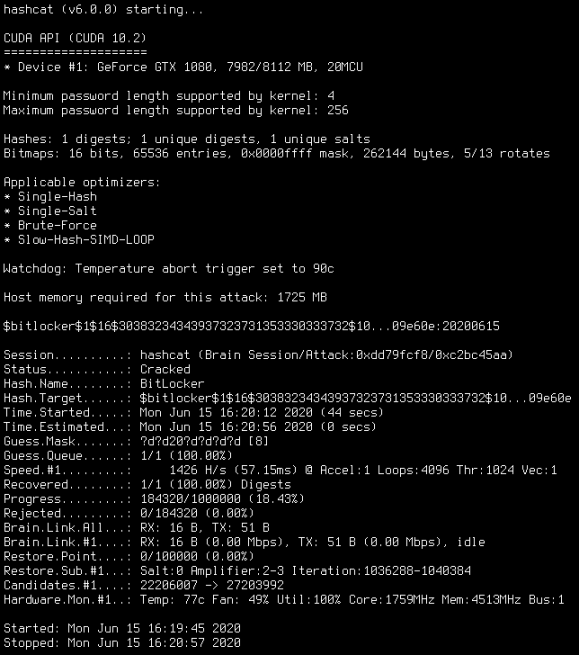
8. Hashcat
Type: Password Cracking Tool
Platform: Windows, Mac OS, Linux
Price: Free (Open Source)
Best For: Cracking and recovering passwords
Link: Link
Description: hashcat is a password recovering and cracking tool. it was closed source before, but became open source since 2015. it also comes pre built in Linux OSes such Kali Linux. some of it’s impressive features:
- Worlds fastest password cracking tool
- World’s first and only in-kernel rule engine
- can crack multiple hashes at a time
- most popular password cracking tool
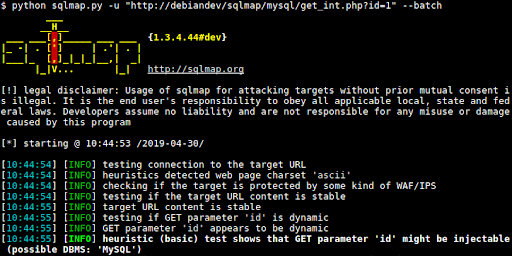
9. SQLMap
Type: SQL Injector
Platform: Cross Platform
Price: Free
Best For: Scanning and injecting SQL into web applications
Link: Link
Description: it’s a tool that comes built in with Kali and other security OSes. it is used to automatically inject sql into web apps and databases. it automates the process of detecting vulnerable sql databases. it comes with powerful engine and many neat features for professional hackers.
Also Read:How To Take Full Control of Somone’s Phone Remotely
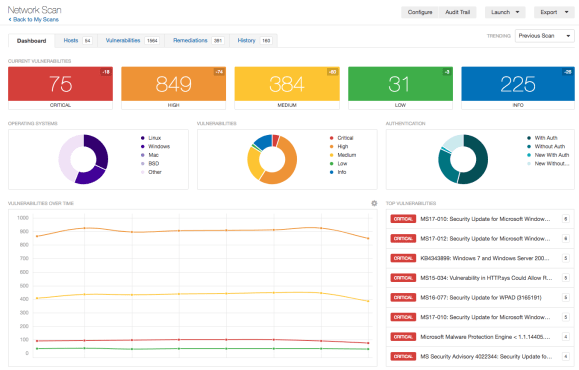
10. Nessus
Type: Vulnerability Scanner
Platform: Windows, Linux, Mac OS
Price: Paid and Free
Best For: Scanning Website’s for Vulnerability
Link: Link
Description: Nesus
11. THC Hydra

Type: Brute Force Software
Platform: Cross Platform
Price: Free
Best For: Brute-Forcing Accounts and files
Link: Link
Description: THC Hyrda, a software that comes built in with Kali Linux, is a software that is used for brute forcing. it can brute force files as well as Social Media Accounts. it is also an Open Source Software
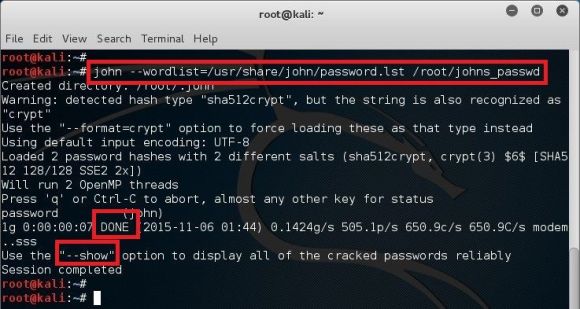
12. John The Ripper
Type: Password Cracker
Platform: Linux and Mac OS (there are suggestions for windows and android by the creater)
Price: Free
Best For: Cracking Passwords
Link: Link
Description: it is a free and open source software that is mainly used for cracking password from encrypted files such as WinRar and the likes of it.
